Best RemoteIoT Web SSH: Your Ultimate Guide To Secure Remote Access
In today's digital era, secure remote access has become more crucial than ever, especially for managing IoT devices. Best RemoteIoT web SSH solutions play a pivotal role in ensuring that your network remains protected while providing seamless access to remote systems. Whether you're a tech enthusiast or a professional, understanding the importance of secure remote access is essential for maintaining the integrity of your digital infrastructure.
As more businesses adopt IoT technologies, the demand for robust remote access solutions continues to grow. However, with this growth comes the challenge of ensuring security and privacy. Best RemoteIoT web SSH solutions are designed to address these challenges, offering a secure and efficient way to manage your IoT devices from anywhere in the world.
This comprehensive guide will walk you through everything you need to know about secure remote access using RemoteIoT web SSH. From understanding the basics to exploring advanced features, we'll cover it all to help you make informed decisions for your business or personal needs.
Read also:Greg Gutfeld Wife A Closer Look At His Personal Life And Marriage
Table of Contents
- Introduction to RemoteIoT Web SSH
- The Importance of Secure Remote Access
- Understanding the Basics of RemoteIoT Web SSH
- Key Benefits of Best RemoteIoT Web SSH
- Enhancing Security with RemoteIoT Web SSH
- How to Set Up RemoteIoT Web SSH
- Top Features of Best RemoteIoT Web SSH Solutions
- Comparison of Popular RemoteIoT Web SSH Tools
- Common Issues and Troubleshooting Tips
- The Future of RemoteIoT Web SSH
- Conclusion
Introduction to RemoteIoT Web SSH
RemoteIoT web SSH is a powerful solution that allows users to access and manage IoT devices remotely through a secure web interface. This technology has revolutionized the way businesses and individuals interact with their IoT networks, offering unparalleled convenience and security. By leveraging SSH (Secure Shell) protocols, RemoteIoT web SSH ensures that all communications between devices are encrypted and protected from unauthorized access.
One of the primary advantages of RemoteIoT web SSH is its ability to provide a user-friendly interface that simplifies complex tasks. Whether you're monitoring sensors, configuring devices, or troubleshooting issues, this solution makes it easy to manage your IoT infrastructure from anywhere in the world. Additionally, its compatibility with various platforms and devices ensures that it can be integrated into existing systems seamlessly.
Why Choose RemoteIoT Web SSH?
When compared to traditional remote access methods, RemoteIoT web SSH offers several key advantages. First, it provides a higher level of security, ensuring that sensitive data remains protected at all times. Second, its web-based interface eliminates the need for specialized software, making it accessible to users of all skill levels. Finally, its scalability allows it to grow alongside your business, accommodating increasing demands without compromising performance.
The Importance of Secure Remote Access
In today's interconnected world, secure remote access is no longer a luxury but a necessity. With the rise of cyber threats and data breaches, ensuring the security of your IoT devices is critical for protecting sensitive information and maintaining operational continuity. Best RemoteIoT web SSH solutions address these concerns by providing a secure and reliable way to access your devices remotely.
Secure remote access not only enhances security but also improves productivity. By enabling users to manage their IoT devices from anywhere, businesses can reduce downtime and respond to issues more quickly. This flexibility allows teams to collaborate more effectively, leading to increased efficiency and better decision-making.
Key Security Challenges in Remote Access
- Unauthorized access and hacking attempts
- Data breaches and privacy concerns
- Compatibility issues with different devices and platforms
- Scalability limitations in growing networks
Understanding the Basics of RemoteIoT Web SSH
At its core, RemoteIoT web SSH combines the power of IoT technology with the security of SSH protocols to create a robust remote access solution. SSH, or Secure Shell, is a cryptographic network protocol that facilitates secure communication over unsecured networks. By integrating SSH with IoT devices, RemoteIoT web SSH ensures that all data transmitted between devices is encrypted and protected from interception.
Read also:Streakeez Exploring The Phenomenon Of Japanese Street Fashion Icons
RemoteIoT web SSH operates through a web-based interface, allowing users to access their devices through a standard web browser. This eliminates the need for specialized software, making it easier for users to manage their IoT networks from any device with internet access. Additionally, its support for multiple authentication methods, such as passwords and SSH keys, adds an extra layer of security to the system.
How Does RemoteIoT Web SSH Work?
When you connect to a device using RemoteIoT web SSH, the following steps occur:
- The client initiates a connection to the server using the SSH protocol.
- The server authenticates the client using either a password or an SSH key.
- Once authenticated, the client establishes a secure session with the server.
- Data is transmitted between the client and server through an encrypted channel.
Key Benefits of Best RemoteIoT Web SSH
Best RemoteIoT web SSH solutions offer a wide range of benefits that make them an attractive choice for businesses and individuals alike. From enhanced security to increased flexibility, these solutions provide a comprehensive approach to managing IoT devices remotely. Below are some of the key benefits of using RemoteIoT web SSH:
- Improved security through encryption and authentication
- Seamless integration with existing IoT infrastructure
- Easy-to-use web-based interface for simplified management
- Compatibility with various devices and platforms
- Scalability to accommodate growing networks
Enhancing Productivity with RemoteIoT Web SSH
By enabling users to manage their IoT devices remotely, RemoteIoT web SSH solutions help improve productivity and reduce downtime. Teams can collaborate more effectively, and issues can be resolved faster, leading to increased efficiency and better decision-making.
Enhancing Security with RemoteIoT Web SSH
Security is one of the most critical aspects of any remote access solution, and RemoteIoT web SSH excels in this area. By leveraging SSH protocols, it ensures that all communications between devices are encrypted and protected from unauthorized access. Additionally, its support for multiple authentication methods adds an extra layer of security to the system.
To further enhance security, best practices such as using strong passwords, enabling two-factor authentication, and regularly updating software should be implemented. These measures help protect your IoT devices from potential threats and ensure that your network remains secure at all times.
Best Practices for Secure Remote Access
- Use strong and unique passwords for all accounts
- Enable two-factor authentication for added security
- Regularly update software and firmware to address vulnerabilities
- Limit access to sensitive data and devices
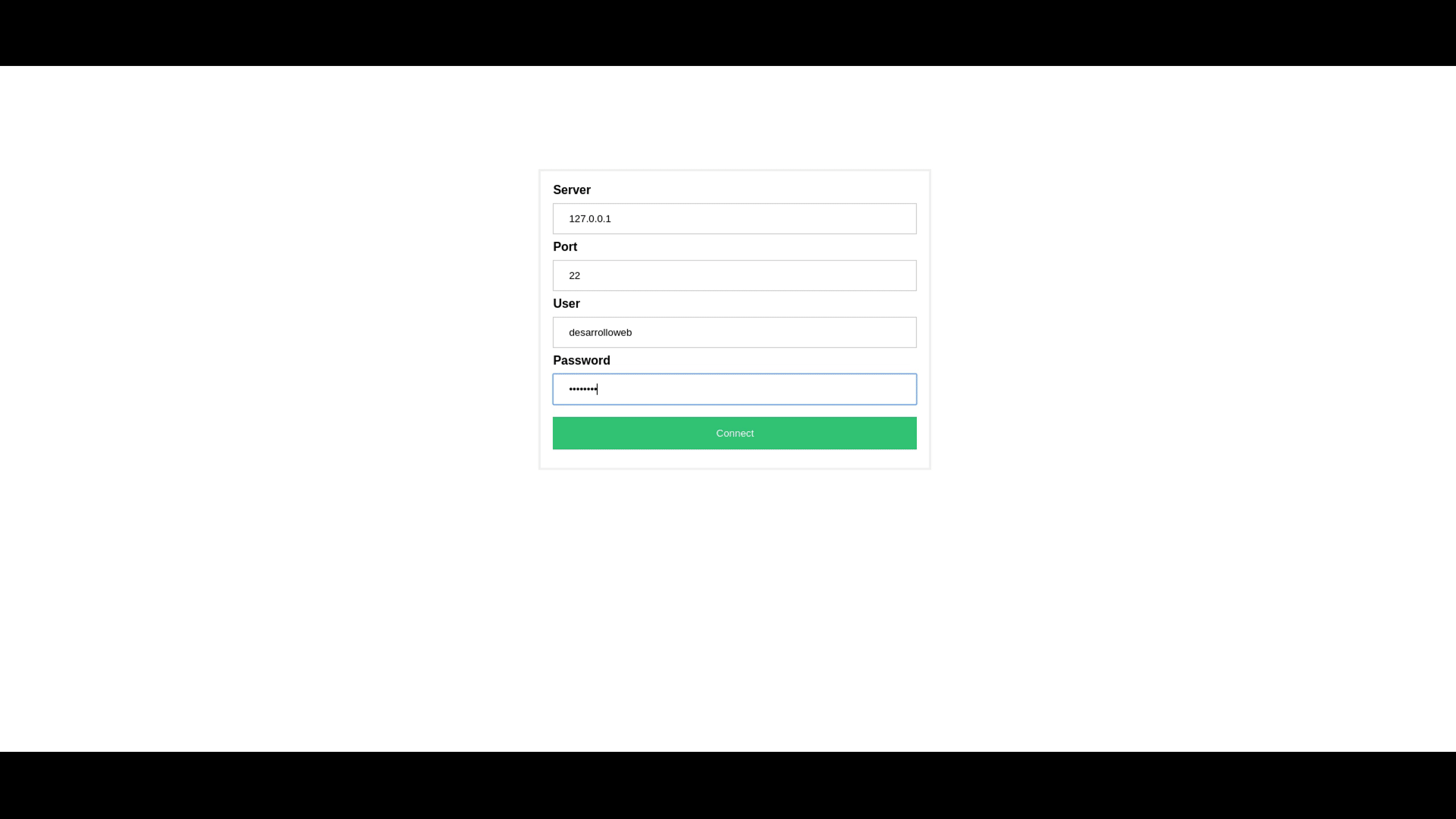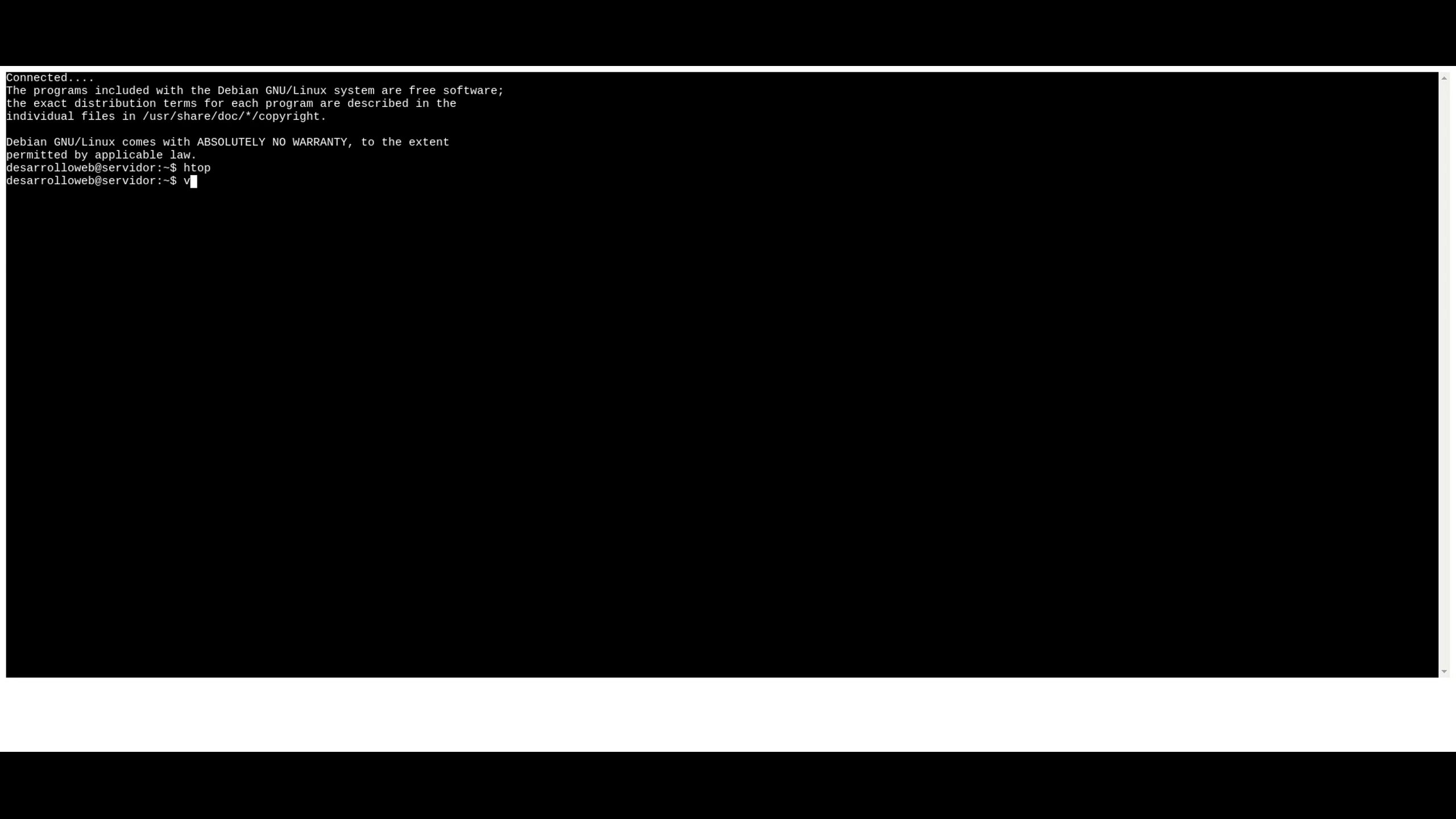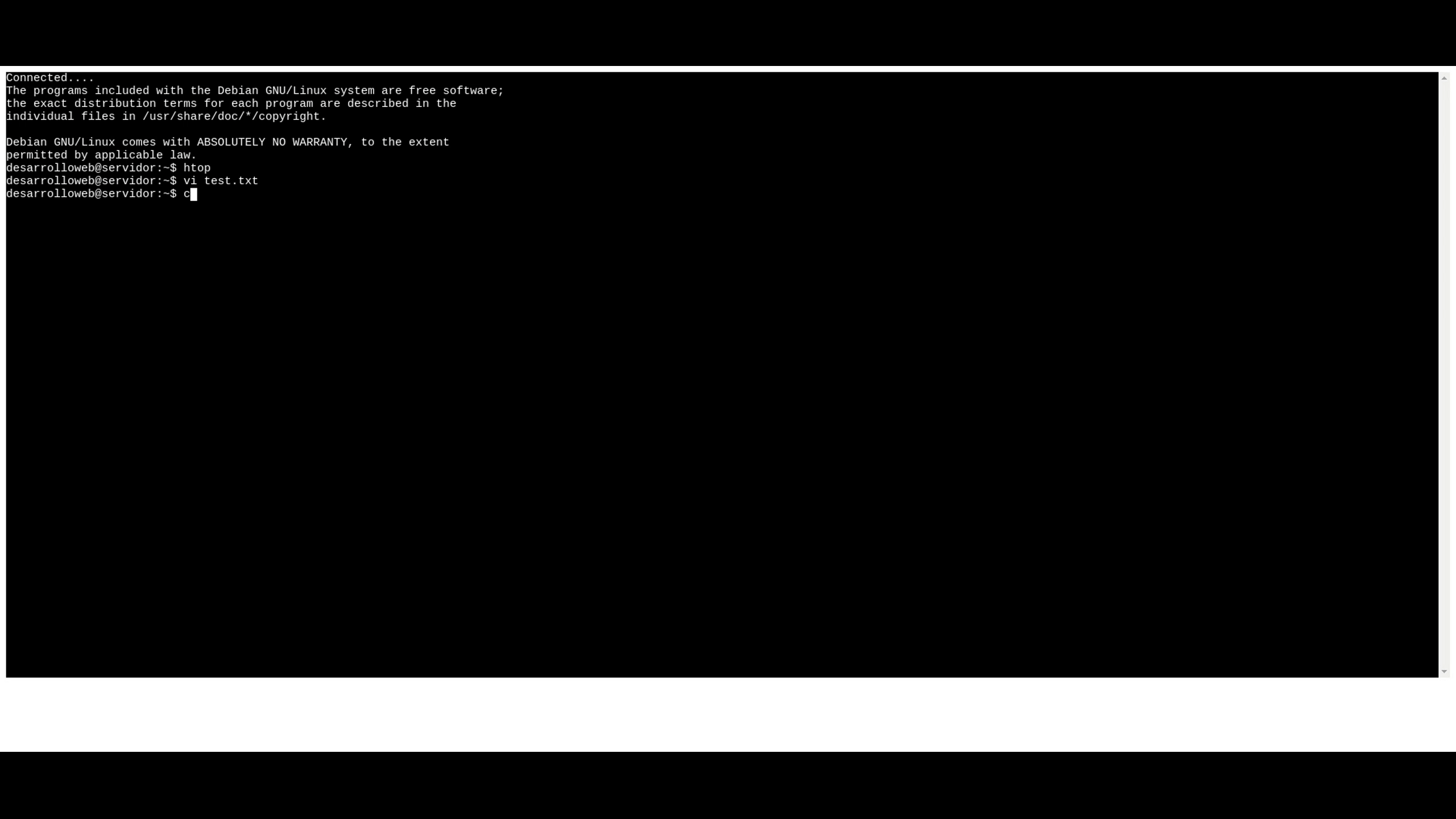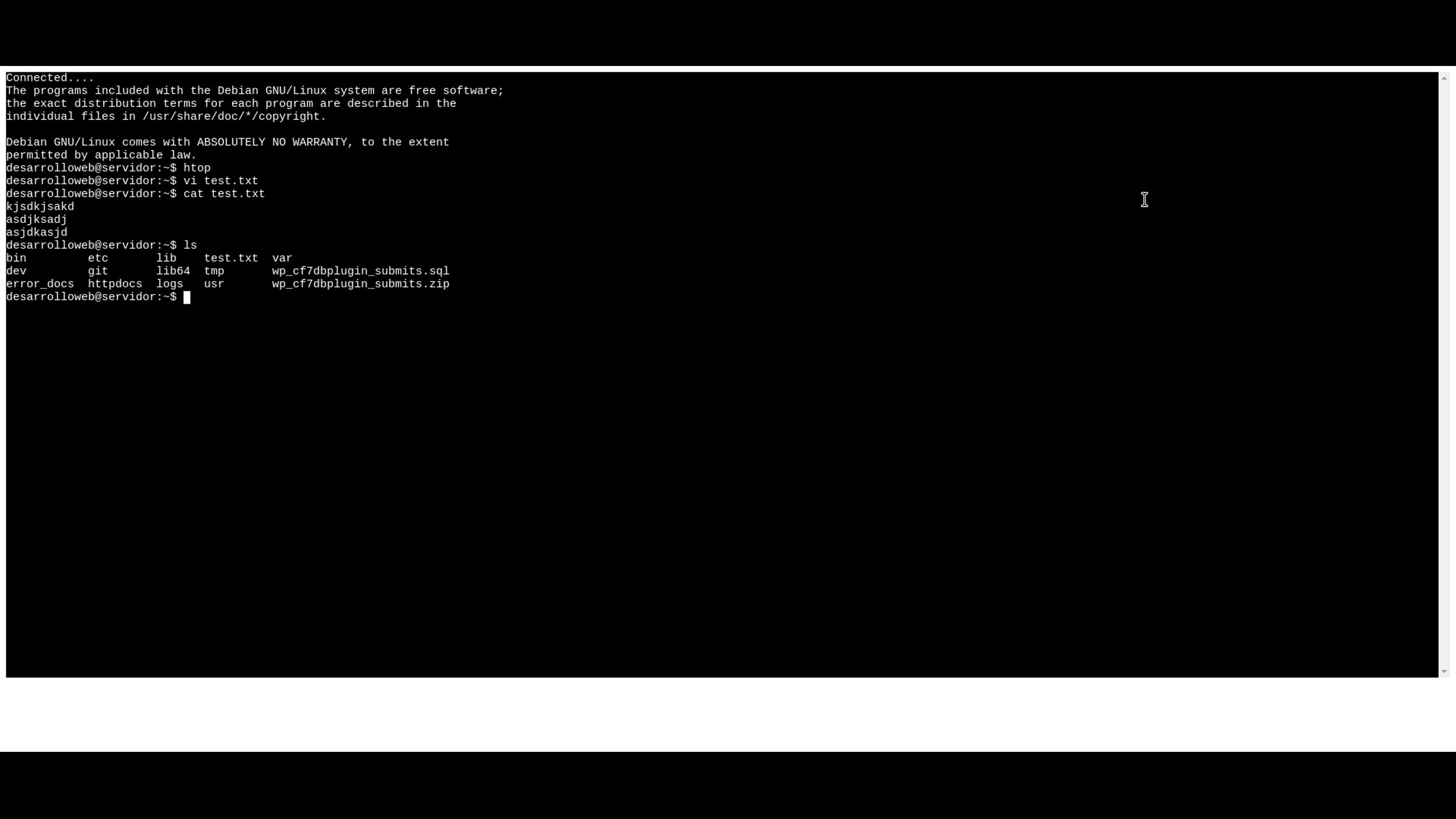
How to Set Up RemoteIoT Web SSH
Setting up RemoteIoT web SSH is a straightforward process that can be completed in just a few steps. Below is a step-by-step guide to help you get started:
- Install the RemoteIoT web SSH software on your server
- Configure the server to accept SSH connections
- Set up user accounts and assign appropriate permissions
- Test the connection to ensure everything is working correctly
Once the setup is complete, you can access your IoT devices remotely through a web browser. This simple and efficient process makes it easy for users to manage their devices from anywhere in the world.
Troubleshooting Common Setup Issues
If you encounter any issues during the setup process, the following tips may help:
- Verify that the server is configured to accept SSH connections
- Check that the correct port number is being used
- Ensure that firewalls and security settings allow SSH traffic
- Consult the documentation for additional troubleshooting tips
Top Features of Best RemoteIoT Web SSH Solutions
Best RemoteIoT web SSH solutions offer a wide range of features that make them an attractive choice for businesses and individuals. Below are some of the top features to look for when selecting a solution:
- Secure SSH-based communication
- Web-based interface for easy management
- Support for multiple authentication methods
- Compatibility with various devices and platforms
- Scalability to accommodate growing networks
Advanced Features to Consider
In addition to the basic features, some RemoteIoT web SSH solutions offer advanced features that can enhance functionality and security. These may include:
- Two-factor authentication for added security
- Role-based access control for fine-grained permissions
- Logging and monitoring for improved accountability
- Integration with third-party tools and services
Comparison of Popular RemoteIoT Web SSH Tools
When selecting a RemoteIoT web SSH solution, it's essential to compare the features and capabilities of different tools to ensure you choose the best option for your needs. Below is a comparison of some of the most popular RemoteIoT web SSH tools:
| Tool | Features | Price | Support |
|---|---|---|---|
| Tool A | Secure SSH, web-based interface, multi-authentication | $49/month | 24/7 live support |
| Tool B | SSH, role-based access, logging | $35/month | Email and chat support |
| Tool C | SSH, web interface, third-party integration | $59/month | 24/7 live support |
Common Issues and Troubleshooting Tips
While RemoteIoT web SSH solutions are generally reliable, users may occasionally encounter issues that require troubleshooting. Below are some common problems and tips for resolving them:
- Connection issues: Verify that the server is configured correctly and that firewalls allow SSH traffic.
- Authentication errors: Ensure that the correct credentials are being used and that two-factor authentication is enabled if required.
- Performance issues: Check for network congestion or hardware limitations that may be affecting performance.
The Future of RemoteIoT Web SSH
As IoT technology continues to evolve, the demand for secure remote access solutions like RemoteIoT web SSH will only grow. Future advancements in encryption, authentication, and user interface design will further enhance the capabilities of these solutions, making them even more secure and user-friendly.
Businesses and individuals alike can look forward to a future where remote access to IoT devices is not only secure but also seamless and intuitive. By staying informed about the latest developments in this field, you can ensure that your IoT infrastructure remains protected and efficient.
Conclusion
In conclusion, best RemoteIoT web SSH solutions offer a comprehensive approach to secure remote access, providing users with the tools they need to manage their IoT devices safely and efficiently. By understanding the basics, exploring the features, and implementing best practices, you can make informed decisions that benefit your business or personal needs.
We invite you to share your thoughts and experiences in the comments below. Additionally, feel free to explore other articles on our site for more information on IoT and related technologies. Together, let's build a secure and connected future!
For further reading, consider exploring resources from trusted sources such as NIST and Cisco.