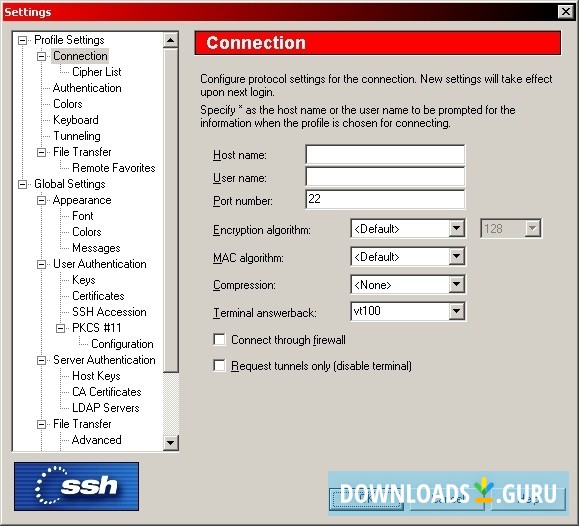
Secure SSH Login For IoT Devices: Download And Setup Guide For MacOS
As the Internet of Things (IoT) continues to expand, securing SSH login for IoT devices has become a top priority for users, especially those on macOS. With the increasing number of cyber threats targeting IoT devices, understanding how to secure SSH connections is essential for maintaining data integrity and privacy. In this guide, we will explore step-by-step instructions to download and set up secure SSH logins for IoT devices on macOS.
Whether you're managing smart home devices, industrial sensors, or remote monitoring systems, securing your IoT devices is crucial. This article will provide you with practical tips, tools, and best practices to ensure your devices are protected against unauthorized access.
By the end of this guide, you will have a comprehensive understanding of how to download and configure SSH for your IoT devices on macOS. Let's dive in!
Read also:Srtay Kids The Ultimate Guide To Understanding And Engaging With The Trend
Table of Contents:
- Introduction to Secure SSH Login
- Why Secure SSH Login is Important for IoT Devices
- Overview of SSH and Its Role in IoT Security
- Setting Up SSH on macOS
- Downloading SSH Tools for macOS
- Step-by-Step Guide to Secure SSH Login
- Best Practices for Securing SSH on macOS
- Common Issues and Troubleshooting Tips
- Alternative Tools for IoT Security
- Conclusion and Next Steps
Introduction to Secure SSH Login
Secure Shell (SSH) is a cryptographic network protocol used for secure data communication between devices. In the context of IoT devices, SSH ensures that sensitive information exchanged between your devices and the network remains encrypted and protected from unauthorized access.
For macOS users, setting up SSH is relatively straightforward, but ensuring its security requires careful configuration. This section will introduce you to the basics of SSH and why it is critical for IoT devices.
What is SSH?
SSH, or Secure Shell, is a network protocol that provides secure communication between two devices over an unsecured network. It is widely used for remote server management, file transfer, and secure command execution.
Why Secure SSH Login is Important for IoT Devices
In today's digital landscape, IoT devices are increasingly targeted by cybercriminals. Without proper security measures, these devices can become entry points for malicious actors to access your network. Secure SSH login plays a vital role in safeguarding your IoT devices against unauthorized access.
- Prevents Unauthorized Access: SSH ensures that only authorized users can access your IoT devices.
- Encrypts Data Transmission: All data exchanged between devices is encrypted, reducing the risk of data interception.
- Improves Network Security: By securing SSH connections, you enhance the overall security of your network.
Overview of SSH and Its Role in IoT Security
SSH is not just a protocol; it is a comprehensive solution for securing IoT devices. In this section, we will explore the key features of SSH and its role in IoT security.
Read also:Mike Adria The Rising Star In The Entertainment Industry
Key Features of SSH
SSH offers several features that make it an ideal choice for securing IoT devices:
- Authentication: SSH supports various authentication methods, including passwords, public key authentication, and two-factor authentication.
- Encryption: SSH encrypts all data transmitted between devices, ensuring confidentiality and integrity.
- Command Execution: SSH allows secure execution of commands on remote devices, making it ideal for managing IoT devices.
Setting Up SSH on macOS
macOS comes pre-installed with SSH, making it easy for users to set up secure connections. In this section, we will guide you through the process of enabling SSH on macOS.
Enabling SSH on macOS
To enable SSH on macOS, follow these steps:
- Open System Preferences and navigate to Sharing.
- Select Remote Login from the list of services.
- Ensure that the checkbox for Remote Login is selected.
Downloading SSH Tools for macOS
While macOS includes built-in SSH support, there are several third-party tools that can enhance your SSH experience. In this section, we will discuss some popular SSH tools for macOS.
Popular SSH Tools
- Terminal: The built-in terminal application on macOS is a powerful tool for SSH connections.
- Termius: A user-friendly SSH client that offers advanced features like session management and key storage.
- PuTTY: Although primarily designed for Windows, PuTTY is also available for macOS and offers robust SSH functionality.
Step-by-Step Guide to Secure SSH Login
Now that you have enabled SSH on macOS, it's time to configure it for secure IoT device management. Follow these steps to ensure a secure SSH login:
Step 1: Generate SSH Keys
SSH keys provide a more secure alternative to password-based authentication. To generate SSH keys on macOS, open the terminal and run the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
Step 2: Copy Public Key to IoT Device
Once you have generated your SSH keys, copy the public key to your IoT device using the following command:
ssh-copy-id user@iot_device_ip
Step 3: Configure SSH Settings
Modify the SSH configuration file on your IoT device to enhance security. Open the file using the following command:
sudo nano /etc/ssh/sshd_config
Make the following changes:
- Set
PermitRootLogin noto disable root login. - Set
PasswordAuthentication noto disable password-based authentication.
Best Practices for Securing SSH on macOS
To ensure the highest level of security for your SSH connections, follow these best practices:
- Use Strong Passwords: If you must use password-based authentication, ensure your passwords are strong and unique.
- Enable Two-Factor Authentication: Add an extra layer of security by enabling two-factor authentication.
- Regularly Update Software: Keep your macOS and SSH tools up to date to protect against vulnerabilities.
Common Issues and Troubleshooting Tips
Despite following best practices, you may encounter issues while setting up SSH on macOS. In this section, we will address some common problems and provide troubleshooting tips.
Issue: Connection Timeout
If you experience connection timeouts, check the following:
- Ensure that the IoT device's firewall allows SSH traffic.
- Verify that the correct IP address and port number are used.
Alternative Tools for IoT Security
While SSH is a powerful tool for securing IoT devices, there are other options worth considering:
- TLS/SSL: Transport Layer Security (TLS) and Secure Sockets Layer (SSL) provide secure communication protocols for IoT devices.
- VPN: Virtual Private Networks (VPNs) can enhance security by creating encrypted tunnels for data transmission.
Conclusion and Next Steps
Securing SSH login for IoT devices on macOS is a critical step in protecting your network from cyber threats. By following the steps outlined in this guide, you can ensure that your devices remain safe and secure.
We encourage you to take the following actions:
- Review and implement the best practices discussed in this article.
- Explore alternative tools for IoT security to find the best solution for your needs.
- Leave a comment or share this article with others who may benefit from it.
Stay secure and keep your IoT devices protected!