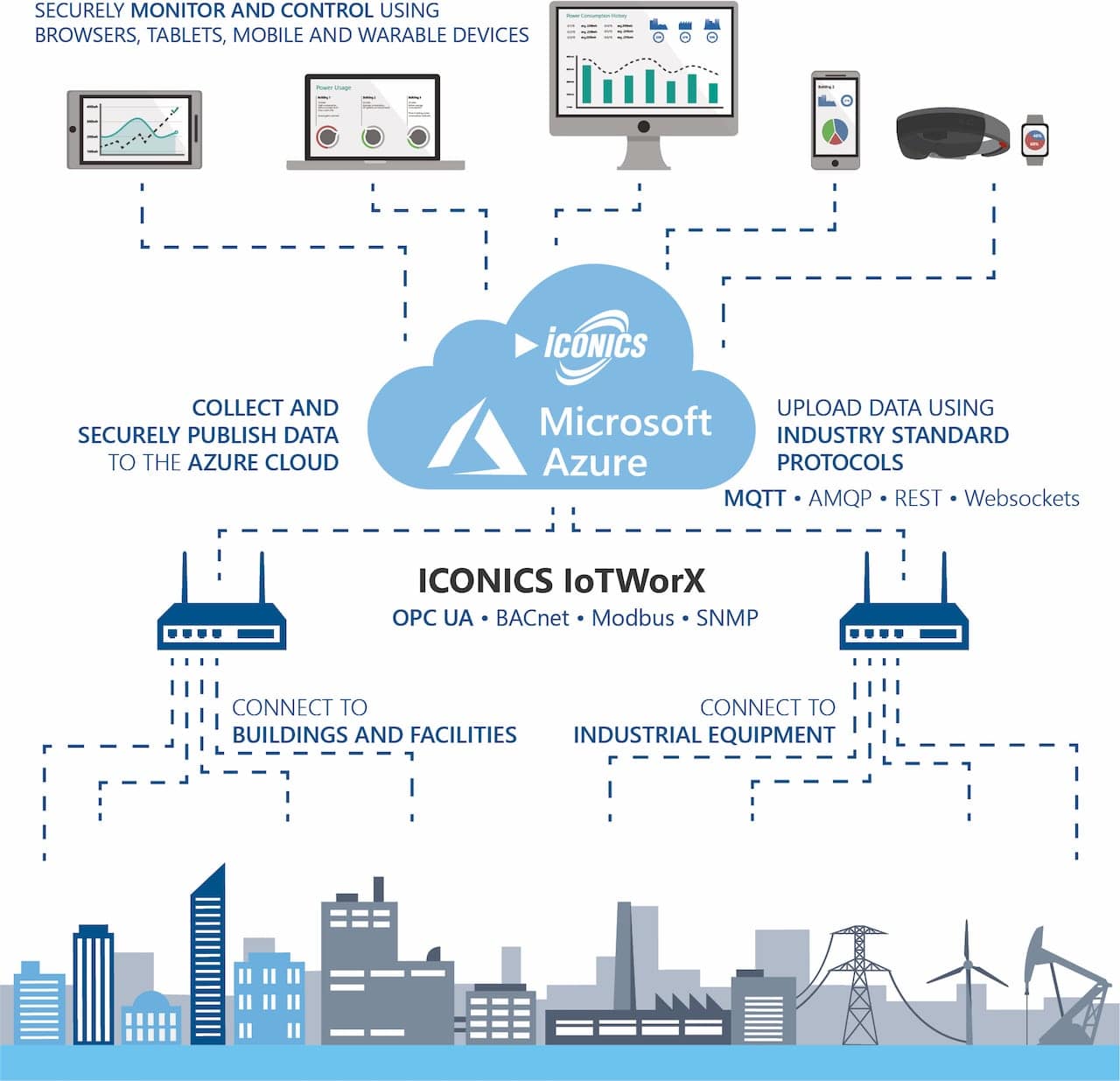
Securely Connect Remote IoT VPC: The Ultimate Guide For Network Security
In today's interconnected world, securely connect remote IoT VPC has become a critical concern for businesses and organizations of all sizes. The rise of Internet of Things (IoT) devices and the increasing reliance on cloud computing have created new challenges in maintaining robust network security. Understanding how to establish secure connections between remote IoT devices and Virtual Private Clouds (VPCs) is not only essential but also crucial for safeguarding sensitive data and maintaining operational integrity.
As more companies adopt IoT technologies, the need for secure communication channels grows exponentially. This article serves as a comprehensive guide to help you navigate the complexities of securing remote IoT VPC connections. We'll explore the latest strategies, tools, and best practices to ensure your network remains protected against potential threats.
Whether you're a network administrator, IT professional, or decision-maker looking to enhance your organization's security posture, this guide will provide actionable insights to help you achieve a secure IoT VPC environment. Let's delve into the details and equip you with the knowledge to protect your digital assets effectively.
Read also:Karl Thomas Dean The Dynamic Mayor Of Nashville
Table of Contents
- Introduction to IoT VPC
- Importance of Securing IoT VPC
- Key Challenges in IoT VPC Security
- Best Practices for Securing IoT VPC
- Tools and Technologies for Secure Connections
- Network Architecture for Secure IoT VPC
- Data Protection and Encryption
- Monitoring and Threat Detection
- Compliance and Regulatory Considerations
- Future Trends in IoT VPC Security
- Conclusion and Next Steps
Introduction to IoT VPC
Understanding IoT and VPC
The Internet of Things (IoT) refers to the network of physical devices, vehicles, appliances, and other items embedded with sensors, software, and connectivity that enables them to exchange data. A Virtual Private Cloud (VPC) is an isolated section of a cloud environment where businesses can deploy and manage their resources securely. When combined, IoT and VPC create a powerful framework for managing and securing large-scale connected systems.
To securely connect remote IoT VPC, it's essential to understand the fundamental components of both technologies. IoT devices generate vast amounts of data, which need to be transmitted securely to a VPC for processing and storage. This connection must be robust enough to handle high volumes of data while maintaining security and reliability.
Benefits of IoT VPC Integration
Integrating IoT with VPC offers several benefits, including enhanced scalability, improved data management, and increased security. By leveraging the capabilities of a VPC, organizations can ensure that their IoT devices operate in a secure and controlled environment, reducing the risk of unauthorized access and data breaches.
Importance of Securing IoT VPC
Securing remote IoT VPC is vital for protecting sensitive data and maintaining the integrity of connected systems. Without proper security measures, IoT devices can become vulnerable to cyberattacks, leading to data breaches, system downtime, and financial losses. Implementing robust security protocols ensures that your IoT VPC environment remains protected against potential threats.
Key Security Concerns
Some of the primary security concerns when securely connecting remote IoT VPC include unauthorized access, data interception, and malware attacks. These threats can compromise the security of your network and lead to significant consequences for your organization. Addressing these concerns requires a comprehensive approach to network security.
Key Challenges in IoT VPC Security
Device Authentication
One of the biggest challenges in securing IoT VPC is ensuring proper device authentication. With thousands of devices connecting to a VPC, it's crucial to verify the identity of each device to prevent unauthorized access. Implementing strong authentication mechanisms is essential for maintaining the security of your IoT VPC environment.
Read also:Aaron Rodgers Wife A Comprehensive Look Into Her Life And Their Relationship
Data Encryption
Encrypting data transmitted between IoT devices and VPCs is another critical challenge. Without proper encryption, sensitive information can be intercepted and exploited by malicious actors. Using advanced encryption protocols helps protect data in transit and at rest, ensuring its confidentiality and integrity.
Best Practices for Securing IoT VPC
Network Segmentation
Segmenting your network is an effective way to enhance security when securely connecting remote IoT VPC. By dividing your network into smaller, isolated segments, you can limit the potential impact of a security breach. This approach also simplifies monitoring and management, making it easier to identify and respond to threats.
Regular Security Audits
Conducting regular security audits is essential for maintaining a secure IoT VPC environment. These audits help identify vulnerabilities and ensure that security measures remain effective over time. By addressing potential issues proactively, you can minimize the risk of security breaches and protect your organization's assets.
Tools and Technologies for Secure Connections
Firewalls and Intrusion Detection Systems
Implementing firewalls and intrusion detection systems (IDS) is crucial for securing remote IoT VPC connections. These tools help monitor network traffic and detect potential threats, allowing you to respond quickly to security incidents. Using advanced firewalls and IDS solutions ensures that your network remains protected against a wide range of threats.
Virtual Private Networks (VPNs)
Using Virtual Private Networks (VPNs) is another effective way to securely connect remote IoT VPC. VPNs create encrypted tunnels for data transmission, ensuring that sensitive information remains protected from unauthorized access. By leveraging VPN technology, you can enhance the security of your IoT VPC environment and safeguard your digital assets.
Network Architecture for Secure IoT VPC
Designing a Secure Network Infrastructure
Creating a secure network architecture is essential for securely connecting remote IoT VPC. This involves designing a robust infrastructure that incorporates multiple layers of security, including firewalls, encryption, and authentication mechanisms. A well-designed network architecture helps protect against potential threats and ensures the reliability of your IoT VPC environment.
Scalability and Flexibility
When designing a network architecture for secure IoT VPC, it's important to consider scalability and flexibility. As your organization grows and adopts new technologies, your network infrastructure must be able to adapt to changing demands. Building a scalable and flexible network ensures that your IoT VPC environment remains secure and efficient over time.
Data Protection and Encryption
Data Encryption Protocols
Using advanced data encryption protocols is crucial for protecting sensitive information when securely connecting remote IoT VPC. Protocols such as AES and TLS provide strong encryption for data in transit and at rest, ensuring its confidentiality and integrity. Implementing these protocols helps safeguard your organization's digital assets and maintain the security of your IoT VPC environment.
Key Management
Effective key management is essential for maintaining the security of encrypted data. By implementing robust key management practices, you can ensure that encryption keys remain secure and are used appropriately. This helps protect your data from unauthorized access and maintains the integrity of your IoT VPC environment.
Monitoring and Threat Detection
Real-Time Monitoring
Implementing real-time monitoring solutions is crucial for detecting potential threats when securely connecting remote IoT VPC. These solutions enable you to monitor network traffic and identify suspicious activity, allowing you to respond quickly to security incidents. Real-time monitoring enhances the security of your IoT VPC environment and helps protect your organization's assets.
Automated Threat Detection
Using automated threat detection tools can significantly improve the security of your IoT VPC environment. These tools analyze network traffic and behavior patterns to identify potential threats, providing early warnings of security incidents. By leveraging automated threat detection, you can enhance the security of your network and minimize the risk of data breaches.
Compliance and Regulatory Considerations
GDPR and CCPA Compliance
Ensuring compliance with data protection regulations such as GDPR and CCPA is essential when securely connecting remote IoT VPC. These regulations require organizations to implement robust security measures to protect personal data and ensure privacy. By adhering to these regulations, you can maintain the trust of your customers and avoid potential legal consequences.
Industry Standards
Adhering to industry standards for network security is crucial for maintaining a secure IoT VPC environment. Standards such as ISO 27001 and NIST provide guidelines for implementing effective security measures and best practices. By following these standards, you can enhance the security of your network and ensure compliance with relevant regulations.
Future Trends in IoT VPC Security
Artificial Intelligence and Machine Learning
The use of artificial intelligence (AI) and machine learning (ML) in IoT VPC security is expected to grow significantly in the coming years. These technologies can help detect and respond to threats more effectively, enhancing the security of connected systems. By leveraging AI and ML, organizations can stay ahead of emerging threats and protect their digital assets.
Blockchain Technology
Blockchain technology offers promising potential for enhancing the security of IoT VPC connections. By providing a decentralized and tamper-proof ledger, blockchain can help ensure the integrity of data transmitted between IoT devices and VPCs. As this technology continues to evolve, it may become an essential component of secure IoT VPC environments.
Conclusion and Next Steps
In conclusion, securely connecting remote IoT VPC requires a comprehensive approach to network security. By implementing best practices, leveraging advanced tools and technologies, and staying informed about emerging trends, you can protect your organization's digital assets and maintain the integrity of your IoT VPC environment. Remember to conduct regular security audits, adhere to industry standards, and ensure compliance with relevant regulations.
We encourage you to take action by reviewing your current security measures and identifying areas for improvement. Share your thoughts and experiences in the comments section below, and feel free to explore other articles on our site for more insights into network security and IoT technologies. Together, we can build a safer and more secure digital future.