How To Use RemoteIoT Behind Firewall Using Mac Server
In the rapidly evolving world of technology, leveraging IoT devices while maintaining network security is a top priority for businesses and individuals alike. One of the challenges many face is using RemoteIoT behind a firewall, especially when utilizing a Mac server. This article will guide you step-by-step on how to configure and secure your setup effectively.
As more organizations adopt IoT technology, understanding how to navigate firewalls and secure servers becomes increasingly important. Whether you're a tech enthusiast or an IT professional, learning how to use RemoteIoT behind a firewall can significantly enhance your network's capabilities.
In this comprehensive guide, we will explore the intricacies of setting up RemoteIoT with a Mac server, ensuring optimal performance and security. By the end of this article, you'll have a clear understanding of the process and the tools required to achieve a seamless setup.
Read also:Unveiling The Mysteries Of Inskz A Comprehensive Guide
Understanding RemoteIoT and Its Benefits
RemoteIoT is a versatile tool designed to facilitate communication between IoT devices and servers, even in restricted environments. It allows users to manage and monitor devices remotely, which is particularly useful for businesses that rely on IoT technology for their operations.
Using RemoteIoT behind a firewall can present challenges, but with the right configuration, it becomes a powerful asset. Below are some benefits of using RemoteIoT:
- Enhanced Security: By configuring RemoteIoT correctly, you can ensure that your IoT devices remain secure even when accessed remotely.
- Improved Efficiency: Remote management of IoT devices streamlines operations, reducing the need for physical intervention.
- Scalability: RemoteIoT can handle a growing number of devices without compromising performance.
Understanding these benefits is crucial before diving into the setup process.
Why Use a Mac Server for RemoteIoT
A Mac server offers several advantages when it comes to managing RemoteIoT behind a firewall. The macOS ecosystem provides robust security features and seamless integration with other Apple devices, making it an ideal choice for this setup.
Key Advantages of Using a Mac Server
- Security: Mac servers come equipped with advanced security protocols that protect against unauthorized access.
- Compatibility: macOS is highly compatible with various IoT devices, ensuring smooth communication.
- User-Friendly Interface: The intuitive design of macOS makes it easy for users to configure and manage their servers.
These advantages make the Mac server a reliable option for deploying RemoteIoT in a secure environment.
Setting Up RemoteIoT on a Mac Server
Before diving into the configuration process, it's essential to prepare your Mac server and ensure it meets the necessary requirements. Follow these steps to set up RemoteIoT effectively:
Read also:Jon Manfrellotti Net Worth A Comprehensive Look Into His Wealth And Success
Step 1: Install macOS Server App
The first step is to install the macOS Server app on your Mac. This app provides the necessary tools to configure and manage your server.
- Download the macOS Server app from the App Store.
- Launch the app and follow the installation instructions.
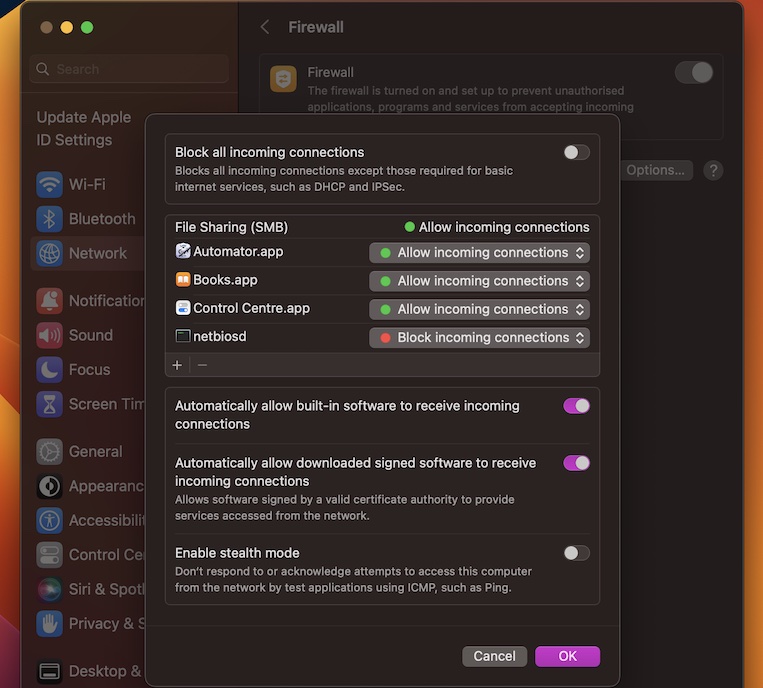
Step 2: Configure Firewall Settings
Configuring your firewall is crucial to ensure that RemoteIoT can operate seamlessly behind it. Follow these steps:
- Open System Preferences and navigate to Security & Privacy.
- Go to the Firewall tab and click on Firewall Options.
- Add the necessary ports for RemoteIoT communication.
Step 3: Install RemoteIoT Software
Once your server is ready, install the RemoteIoT software. Ensure that the software is compatible with your macOS version and follow the installation guide provided by the developer.
Securing Your RemoteIoT Setup
Security should be a top priority when setting up RemoteIoT behind a firewall. Below are some best practices to enhance the security of your setup:
Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security to your RemoteIoT setup. Enable this feature to prevent unauthorized access.
Regularly Update Software
Keeping your software up to date is crucial for maintaining security. Regular updates ensure that any vulnerabilities are patched promptly.
Monitor Network Activity
Regularly monitoring your network activity can help identify any suspicious behavior. Use tools like macOS Server's built-in monitoring features to keep an eye on your network.
Troubleshooting Common Issues
Despite careful configuration, issues may arise when setting up RemoteIoT behind a firewall. Below are some common problems and their solutions:
Issue: Unable to Connect to IoT Devices
If you're unable to connect to your IoT devices, check the following:
- Ensure that the necessary ports are open in your firewall settings.
- Verify that the RemoteIoT software is properly installed and configured.
Issue: Slow Communication
Slow communication between your Mac server and IoT devices can be frustrating. To address this issue:
- Optimize your network settings for better performance.
- Consider upgrading your internet connection if necessary.
Advanced Configuration Tips
For users seeking to maximize the potential of their RemoteIoT setup, here are some advanced configuration tips:
Implement VLANs for Network Segmentation
Using VLANs can help segment your network, improving security and performance. Configure VLANs in your network settings to isolate IoT traffic from other network activity.
Use SSL/TLS Encryption
Encrypting communication between your Mac server and IoT devices ensures that sensitive data remains secure. Enable SSL/TLS encryption in your RemoteIoT settings.
Case Studies: Successful RemoteIoT Deployments
Learning from real-world examples can provide valuable insights into deploying RemoteIoT effectively. Below are some case studies of successful RemoteIoT deployments:
Case Study 1: Smart Home Automation
A homeowner successfully used RemoteIoT to manage their smart home devices behind a firewall. By configuring their Mac server and ensuring proper security measures, they achieved seamless remote control of their home automation system.
Case Study 2: Industrial IoT Implementation
An industrial company implemented RemoteIoT to monitor and manage their IoT devices in a secure environment. Their Mac server setup allowed for efficient data collection and analysis, improving overall operational efficiency.
Future Trends in RemoteIoT and Mac Server Integration
As technology continues to evolve, the integration of RemoteIoT with Mac servers is likely to become even more advanced. Below are some future trends to watch:
Increased Automation
Automation will play a significant role in future RemoteIoT setups, reducing the need for manual intervention and improving efficiency.
Enhanced Security Features
Mac servers will likely incorporate more advanced security features, ensuring that RemoteIoT setups remain secure against emerging threats.
Conclusion
Using RemoteIoT behind a firewall with a Mac server is a powerful solution for managing IoT devices securely and efficiently. By following the steps outlined in this article, you can configure your setup effectively while maintaining optimal security.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into technology and IoT solutions.
Table of Contents
- Understanding RemoteIoT and Its Benefits
- Why Use a Mac Server for RemoteIoT
- Setting Up RemoteIoT on a Mac Server
- Securing Your RemoteIoT Setup
- Troubleshooting Common Issues
- Advanced Configuration Tips
- Case Studies: Successful RemoteIoT Deployments
- Future Trends in RemoteIoT and Mac Server Integration
- Conclusion

![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)