How To Use RemoteIoT Behind Firewall Using Mac: The Ultimate Guide
In today's interconnected world, accessing IoT devices behind a firewall using a Mac has become a critical skill for professionals and enthusiasts alike. Whether you're managing smart home devices, monitoring industrial equipment, or securing your network, understanding how to use RemoteIoT behind a firewall can significantly enhance your productivity and security. This guide will walk you through everything you need to know to achieve seamless connectivity.
As more businesses and individuals adopt Internet of Things (IoT) technologies, the challenge of accessing these devices securely from remote locations grows. A firewall is a crucial component of network security, but it can also act as a barrier to accessing IoT devices. Learning how to use RemoteIoT behind a firewall on a Mac is not only about overcoming technical challenges but also about ensuring compliance with security protocols.
This article is designed to provide comprehensive insights into setting up and managing RemoteIoT behind a firewall. From understanding the basics to advanced configurations, we'll cover everything step by step. Whether you're a beginner or an experienced professional, this guide will equip you with the knowledge and tools necessary to succeed in this area.
Read also:Andrew Garfields Mother A Closer Look At Her Life And Influence
Table of Contents
- Introduction to RemoteIoT
- Firewall Basics
- Why Use RemoteIoT?
- Mac-Specific Considerations
- Setup Steps for RemoteIoT Behind Firewall
- Security Considerations
- Troubleshooting Common Issues
- Advanced Techniques
- Best Practices for Managing RemoteIoT
- Conclusion
Introduction to RemoteIoT
RemoteIoT is a powerful tool designed to facilitate remote access to IoT devices. It allows users to connect to and manage IoT devices securely, even when they are located behind firewalls or in private networks. The tool is particularly useful for professionals who need to monitor and control IoT devices from anywhere in the world.
Understanding the Basics:
- RemoteIoT supports various protocols, including MQTT, HTTP, and TCP.
- It can be configured to work with both Windows and macOS systems.
- Security features such as encryption and authentication are built into the platform.
Key Features of RemoteIoT
RemoteIoT offers several key features that make it an ideal choice for remote IoT management:
- Easy setup and configuration.
- Support for multiple IoT protocols.
- Comprehensive logging and monitoring capabilities.
- Integration with popular cloud platforms.
Firewall Basics
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls are essential for protecting networks from unauthorized access and potential threats.
Types of Firewalls
There are several types of firewalls, each with its own strengths and weaknesses:
- Packet Filtering Firewalls: Examine packets and allow or block them based on rules.
- Stateful Inspection Firewalls: Track active connections and use this information to make decisions.
- Application-Level Gateways: Operate at the application layer and provide enhanced security.
Why Use RemoteIoT?
Using RemoteIoT behind a firewall offers numerous advantages for both individuals and organizations:
Read also:Staykids The Ultimate Guide To Understanding And Exploring The Phenomenon
- Enhanced security through encrypted connections.
- Improved accessibility to IoT devices from remote locations.
- Streamlined management of multiple devices.
- Reduced downtime and faster troubleshooting.
For Mac users, RemoteIoT provides a seamless experience by integrating with macOS features and offering intuitive interfaces.
Mac-Specific Considerations
When using RemoteIoT on a Mac, there are several considerations to keep in mind:
- Ensure that macOS firewall settings are configured correctly.
- Use macOS-specific tools like Terminal for advanced configurations.
- Take advantage of macOS's built-in security features, such as Gatekeeper and XProtect.
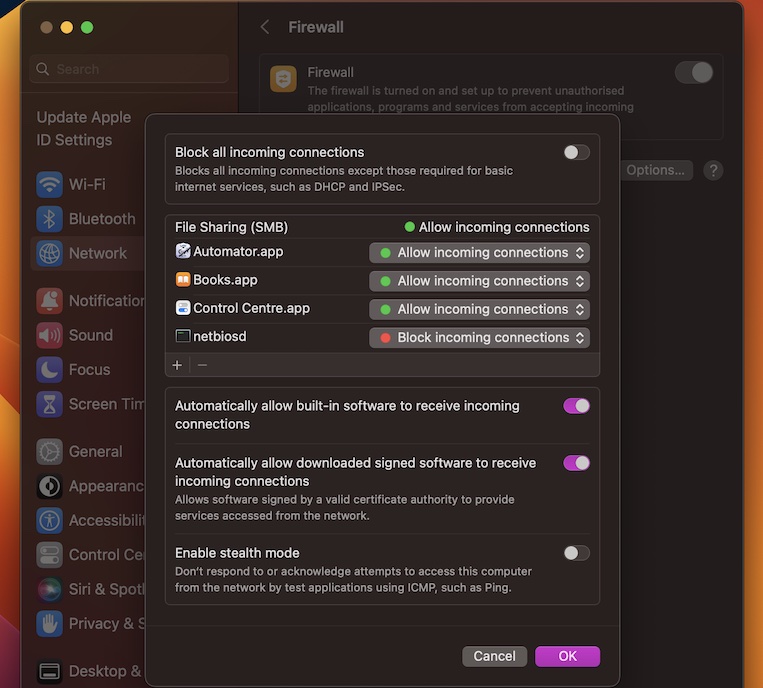
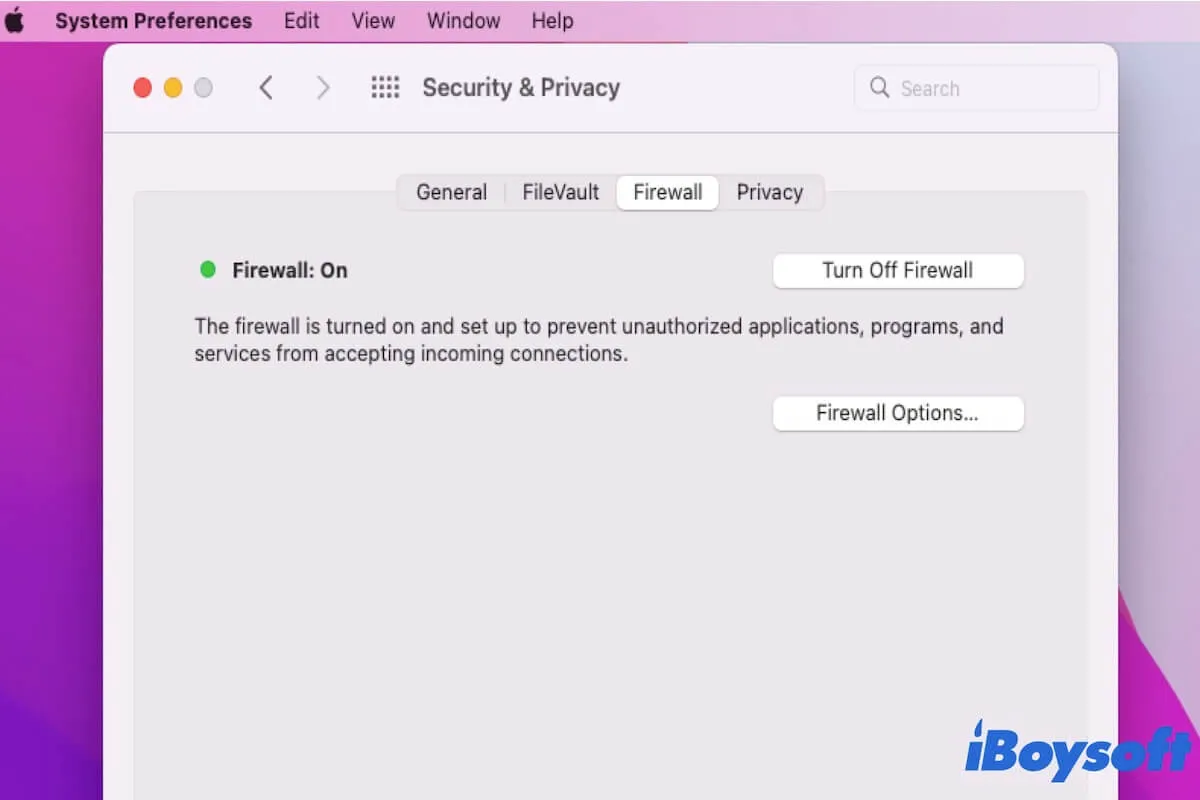
Configuring macOS Firewall
To configure the macOS firewall for RemoteIoT:
- Go to System Preferences > Security & Privacy > Firewall.
- Click the lock icon and enter your password to make changes.
- Enable the firewall and customize settings as needed.
Setup Steps for RemoteIoT Behind Firewall
Setting up RemoteIoT behind a firewall involves several steps:
- Install RemoteIoT software on your Mac.
- Configure the firewall to allow RemoteIoT traffic.
- Set up port forwarding if necessary.
- Test the connection to ensure everything is working correctly.
Step-by-Step Guide
Here's a detailed step-by-step guide:
- Install RemoteIoT: Download and install the latest version of RemoteIoT from the official website.
- Configure Firewall Settings: Adjust your firewall rules to permit RemoteIoT traffic on the required ports.
- Set Up Port Forwarding: If your router supports it, configure port forwarding to direct traffic to your Mac.
- Test the Connection: Use a test device to verify that you can access your IoT devices remotely.
Security Considerations
When using RemoteIoT behind a firewall, security should always be a top priority. Here are some security considerations to keep in mind:
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication (2FA) whenever possible.
- Regularly update software and firmware to protect against vulnerabilities.
Encryption and Authentication
Encryption and authentication are critical components of secure RemoteIoT configurations:
- Encryption: Ensure that all data transmitted between your Mac and IoT devices is encrypted.
- Authentication: Implement robust authentication mechanisms to verify user identities.
Troubleshooting Common Issues
Even with careful planning, issues can arise when setting up RemoteIoT behind a firewall. Here are some common problems and their solutions:
- Connection Issues: Check firewall rules and ensure that the correct ports are open.
- Performance Problems: Optimize network settings and reduce bandwidth usage.
- Security Alerts: Investigate any unusual activity and update security protocols as needed.
Advanced Techniques
For advanced users, there are several techniques that can enhance the functionality of RemoteIoT:
- Implementing VLANs for better network segmentation.
- Using SSH tunnels for secure communication.
- Configuring load balancing to handle high traffic volumes.
SSH Tunneling
SSH tunneling is a powerful technique for securing RemoteIoT connections:
- Establish an SSH connection between your Mac and the target device.
- Route RemoteIoT traffic through the SSH tunnel for added security.
Best Practices for Managing RemoteIoT
To ensure the best possible experience with RemoteIoT, follow these best practices:
- Regularly monitor network activity for signs of unauthorized access.
- Document all configurations and settings for future reference.
- Train team members on proper RemoteIoT usage and security protocols.
Maintaining Security
Security is an ongoing process. Continuously evaluate and update your security measures to stay ahead of potential threats.
Conclusion
In conclusion, using RemoteIoT behind a firewall on a Mac is a powerful way to manage IoT devices securely and efficiently. By following the steps outlined in this guide, you can set up a robust system that meets your needs while maintaining the highest standards of security.
We encourage you to share your thoughts and experiences in the comments section below. If you found this article helpful, please consider sharing it with others who might benefit from it. For more in-depth information on related topics, explore our other articles on our website.