Mastering Remote IoT VPC SSH AWS: The Ultimate Guide For Secure Connectivity
In today's interconnected world, mastering remote IoT VPC SSH AWS connectivity is essential for businesses and individuals alike. As the Internet of Things (IoT) continues to expand, ensuring secure access to cloud resources has become a top priority. This guide will walk you through the fundamentals of establishing a robust and secure connection using AWS Virtual Private Cloud (VPC) and Secure Shell (SSH).
Whether you're a seasoned IT professional or just starting to explore the possibilities of IoT, this ultimate guide will provide you with the knowledge and tools you need to create a secure and efficient remote connectivity setup. By leveraging AWS services, you can enhance your network's security while maintaining flexibility and scalability.
Throughout this article, we'll explore key concepts, best practices, and actionable steps to help you achieve secure connectivity. By the end, you'll have a clear understanding of how to master remote IoT VPC SSH AWS configurations and ensure the protection of your sensitive data.
Read also:Romeo John Bon Jovi The Rising Star In The Spotlight
Table of Contents
- Introduction to Remote IoT VPC SSH AWS
- Basics of AWS VPC
- Understanding SSH and Its Role in IoT
- Securing IoT Devices with AWS VPC and SSH
- Designing Your Network Architecture
- Best Practices for Secure Connectivity
- Troubleshooting Common Issues
- Advanced Features for Enhanced Security
- Managing Costs in AWS VPC SSH Configurations
- Conclusion and Next Steps
Introduction to Remote IoT VPC SSH AWS
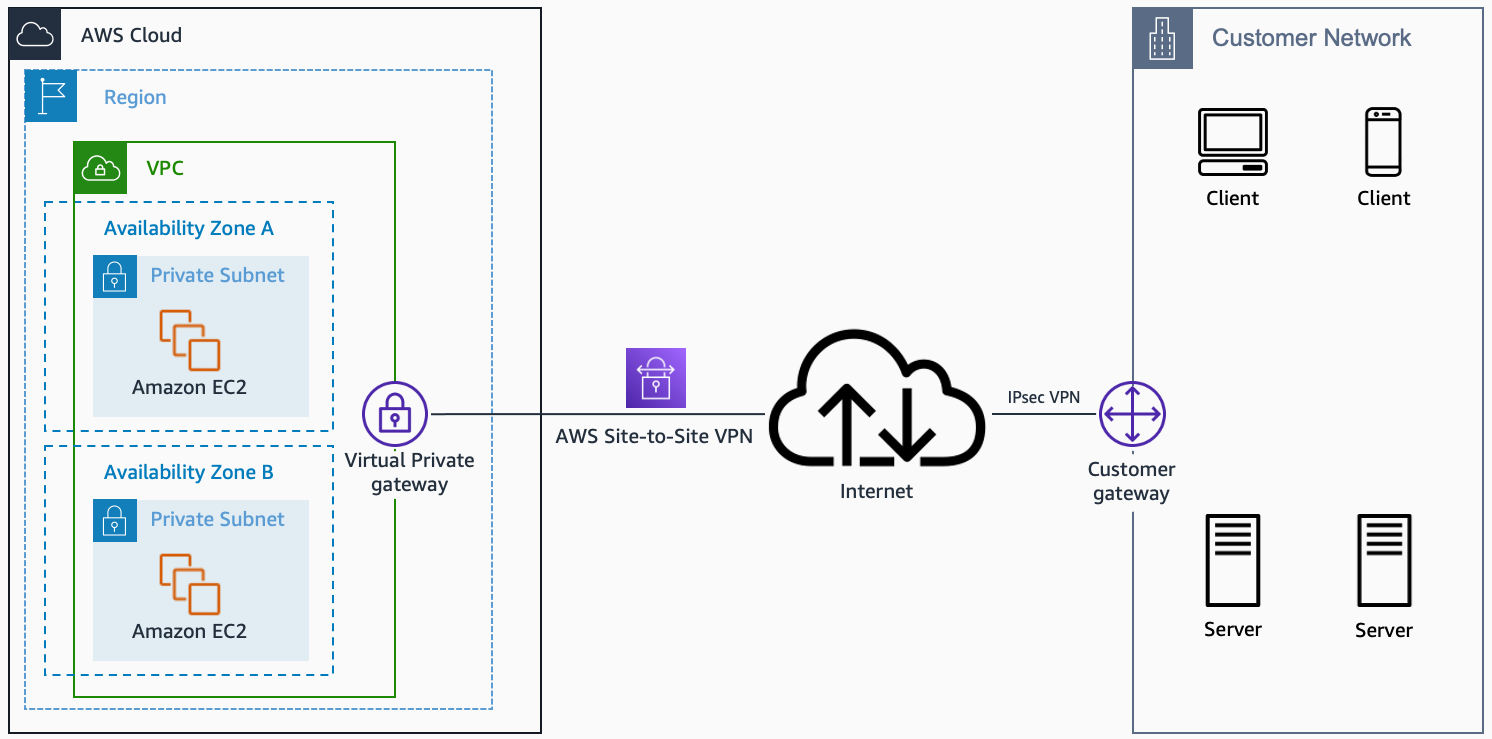
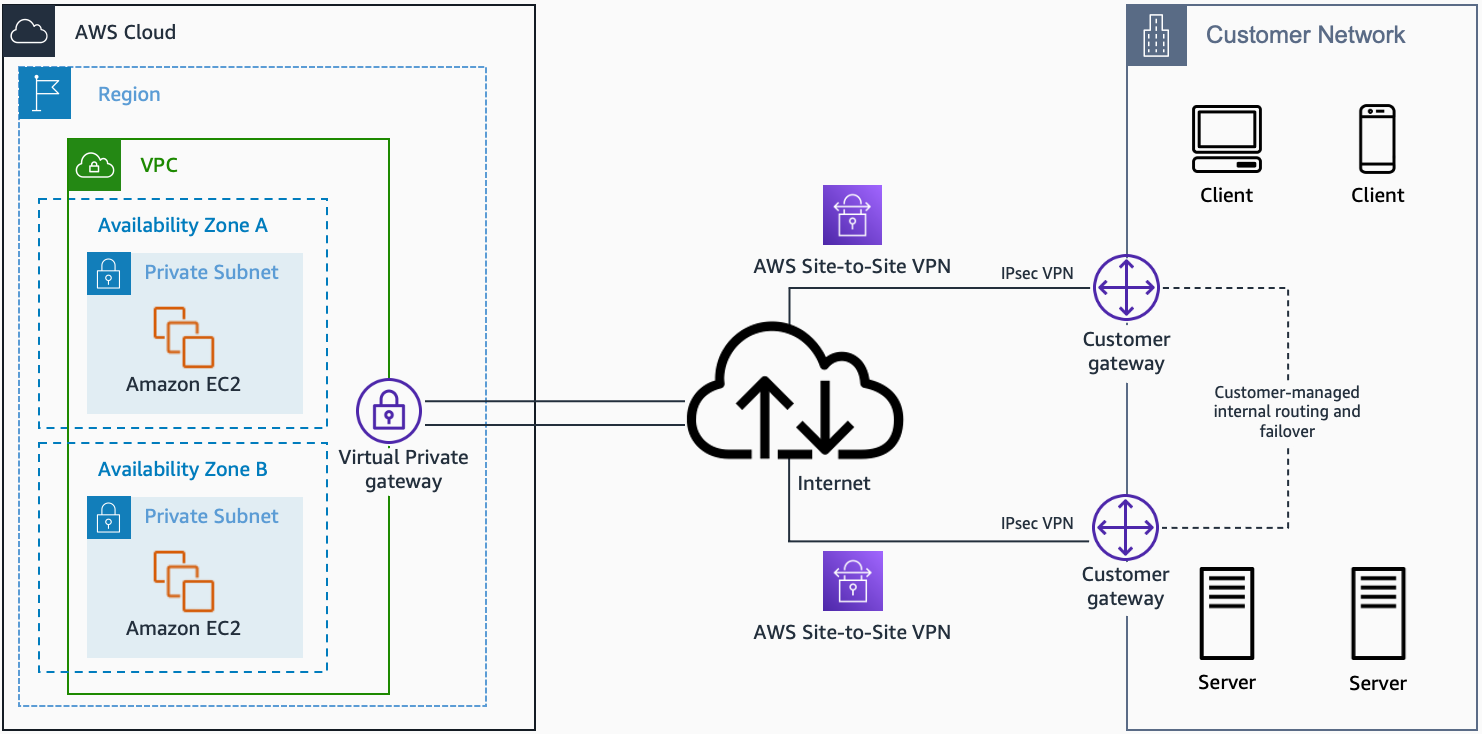
Remote IoT VPC SSH AWS configurations are vital for modern enterprises looking to integrate IoT devices into their cloud infrastructure. AWS Virtual Private Cloud (VPC) offers a secure and isolated environment where IoT devices can communicate seamlessly. Secure Shell (SSH) acts as the backbone for secure remote access, enabling administrators to manage devices and systems without compromising security.
By combining AWS VPC and SSH, organizations can create a robust framework that supports secure connectivity while ensuring compliance with industry standards. This section will introduce the fundamental concepts of AWS VPC and SSH, laying the groundwork for more advanced topics.
As businesses increasingly rely on IoT devices for data collection and automation, the importance of secure remote access cannot be overstated. This guide will equip you with the skills to design, implement, and manage secure remote IoT VPC SSH AWS configurations effectively.
Basics of AWS VPC
What is AWS VPC?
AWS Virtual Private Cloud (VPC) is a service that allows users to create an isolated section of the AWS Cloud. This virtual network closely mirrors the functionality of a traditional data center, providing complete control over IP address ranges, subnets, route tables, and network gateways.
Key Features of AWS VPC
- Isolation: AWS VPC provides a secure and isolated environment for your resources, ensuring that only authorized traffic can access your IoT devices.
- Flexibility: You can define custom IP address ranges, create subnets, and configure routing rules to suit your specific requirements.
- Scalability: AWS VPC supports automatic scaling, allowing you to accommodate growing workloads without compromising performance.
By leveraging AWS VPC, you can create a secure and scalable infrastructure for your IoT devices, ensuring that they remain protected from unauthorized access.
Understanding SSH and Its Role in IoT
What is SSH?
Secure Shell (SSH) is a cryptographic network protocol used for secure communication over unsecured networks. It provides a secure channel for remote access to IoT devices, enabling administrators to manage systems and transfer data without risking interception.
Read also:Haikyuu Battle Of The Garbage Dump The Ultimate Guide To One Of The Most Iconic Matches
Benefits of Using SSH in IoT
- Data Encryption: SSH encrypts all data transmitted between devices, ensuring that sensitive information remains protected.
- Authentication: SSH supports strong authentication mechanisms, such as public key infrastructure (PKI), to verify the identity of users and devices.
- File Transfer: SSH includes the Secure Copy Protocol (SCP) and SFTP, enabling secure file transfers between IoT devices and remote servers.
By integrating SSH into your IoT infrastructure, you can enhance the security of your remote connections and protect your data from potential threats.
Securing IoT Devices with AWS VPC and SSH
Setting Up AWS VPC for IoT Devices
To secure your IoT devices, start by setting up an AWS VPC tailored to your specific needs. Begin by defining a custom IP address range and creating subnets for different device groups. Configure security groups and network access control lists (NACLs) to restrict traffic to authorized sources.
Configuring SSH for IoT Devices
Once your AWS VPC is in place, configure SSH to enable secure remote access to your IoT devices. Generate SSH keys and distribute them securely to authorized users. Configure SSH settings to enforce strong authentication and encryption protocols.
By combining AWS VPC and SSH, you can create a secure and resilient infrastructure for your IoT devices, ensuring that they remain protected from unauthorized access and potential threats.
Designing Your Network Architecture
Best Practices for Network Design
Designing an effective network architecture is crucial for ensuring secure connectivity in a remote IoT VPC SSH AWS setup. Consider the following best practices:
- Segmentation: Use subnets to segment your network and isolate sensitive devices from general traffic.
- Load Balancing: Implement load balancers to distribute traffic evenly across your devices, improving performance and reliability.
- Monitoring: Set up monitoring tools to track network activity and detect potential security threats in real-time.
Implementing Advanced Security Measures
To further enhance the security of your network, consider implementing advanced security measures such as intrusion detection systems (IDS) and firewalls. These tools can help identify and mitigate potential threats before they compromise your IoT devices.
Best Practices for Secure Connectivity
Key Best Practices
To ensure secure connectivity in your remote IoT VPC SSH AWS setup, follow these key best practices:
- Regular Updates: Keep your devices and software up-to-date with the latest security patches and updates.
- Access Control: Implement strict access control policies to limit who can access your IoT devices.
- Encryption: Use encryption protocols to protect sensitive data both in transit and at rest.
By adhering to these best practices, you can create a secure and reliable remote IoT VPC SSH AWS configuration that meets the needs of your organization.
Troubleshooting Common Issues
Common Issues and Solutions
Despite careful planning, issues may arise when setting up remote IoT VPC SSH AWS configurations. Here are some common issues and their solutions:
- Connection Problems: Verify your network settings and ensure that all devices are properly configured.
- Authentication Failures: Check your SSH keys and ensure that they are correctly distributed to authorized users.
- Performance Issues: Optimize your network architecture and implement load balancing to improve performance.
Seeking Professional Assistance
If you encounter persistent issues, consider seeking assistance from AWS support or consulting with a professional network engineer. Their expertise can help resolve complex problems and ensure the smooth operation of your IoT infrastructure.
Advanced Features for Enhanced Security
Exploring Advanced Security Features
AWS offers a range of advanced security features that can further enhance the security of your remote IoT VPC SSH AWS setup. Consider implementing the following features:
- Identity and Access Management (IAM): Use IAM to manage user permissions and ensure that only authorized users can access your resources.
- CloudWatch: Leverage CloudWatch to monitor your infrastructure and detect potential security threats in real-time.
- CloudTrail: Use CloudTrail to track API calls and identify any suspicious activity in your AWS environment.
By taking advantage of these advanced features, you can create a highly secure and resilient IoT infrastructure that meets the demands of modern businesses.
Managing Costs in AWS VPC SSH Configurations
Cost Management Strategies
Managing costs is an essential aspect of maintaining a successful AWS VPC SSH configuration. Consider the following strategies:
- Right-Sizing Resources: Optimize your resource allocation to ensure that you're only using what you need.
- Reserved Instances: Take advantage of reserved instances to reduce costs for long-term resource usage.
- Monitoring Costs: Use AWS Cost Explorer to track your expenses and identify areas for cost savings.
By implementing these cost management strategies, you can ensure that your remote IoT VPC SSH AWS setup remains both secure and cost-effective.
Conclusion and Next Steps
In conclusion, mastering remote IoT VPC SSH AWS configurations is essential for ensuring secure connectivity in today's interconnected world. By following the guidelines and best practices outlined in this ultimate guide, you can create a robust and secure infrastructure for your IoT devices.
We encourage you to take the next steps by experimenting with AWS VPC and SSH configurations in your own environment. Share your experiences and insights in the comments section below, and don't hesitate to explore other articles on our site for more valuable information on IoT and cloud security.
Thank you for reading, and we wish you the best of luck in your journey to mastering remote IoT VPC SSH AWS connectivity!