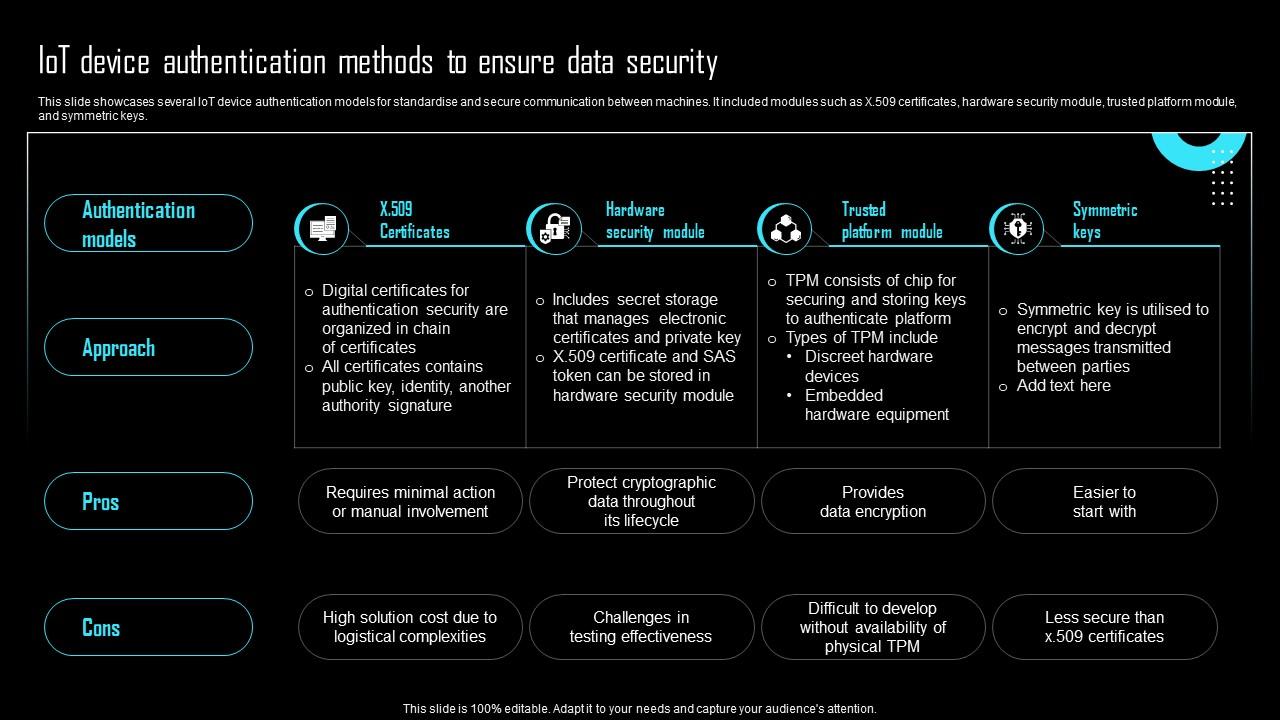
Secure Remote IoT Device Login Using IoT Core: The Ultimate Guide
In today's interconnected world, secure remote IoT device login using IoT Core is more crucial than ever. The Internet of Things (IoT) has revolutionized how we interact with technology, but it also brings unique security challenges. Ensuring secure access to IoT devices remotely is essential to protect sensitive data and maintain system integrity.
As IoT adoption continues to grow, organizations and individuals must prioritize security measures. Secure remote IoT device login using IoT Core offers a robust solution for managing and securing IoT devices. This guide will provide comprehensive insights into this critical topic, ensuring you're well-equipped to safeguard your IoT infrastructure.
By exploring the nuances of IoT Core and its role in secure remote IoT device login, this article will empower you with the knowledge needed to protect your devices from potential threats. Whether you're a developer, IT professional, or enthusiast, understanding these principles is vital for maintaining secure IoT ecosystems.
Read also:Stray Kids A Comprehensive Dive Into Their Journey And Success
Understanding IoT Core and Its Importance
The Internet of Things (IoT) Core plays a pivotal role in managing and securing IoT devices. It serves as a foundational platform that facilitates communication, data processing, and device management. Understanding IoT Core's capabilities is essential for implementing secure remote IoT device login protocols effectively.
What Is IoT Core?
IoT Core is a cloud-based platform designed to connect, manage, and secure IoT devices at scale. It provides a secure environment for device authentication, data transmission, and monitoring. By leveraging IoT Core, organizations can ensure that only authorized devices access their networks, reducing the risk of unauthorized access and data breaches.
Key Features of IoT Core
- Device Authentication: IoT Core ensures that only trusted devices can connect to the network.
- Data Encryption: All data transmitted between devices and the cloud is encrypted, maintaining confidentiality.
- Device Management: IoT Core offers tools for monitoring and managing device health and security.
- Scalability: The platform supports large-scale IoT deployments, making it suitable for enterprises of all sizes.
Challenges in Secure Remote IoT Device Login
While IoT devices offer numerous benefits, securing their remote access poses significant challenges. Understanding these challenges is the first step toward implementing effective security measures.
Common Security Threats
- Unauthorized Access: Hackers may attempt to gain access to IoT devices through weak authentication mechanisms.
- Data Breaches: Sensitive information transmitted between devices and the cloud can be intercepted if not properly encrypted.
- Device Hijacking: Malicious actors can take control of IoT devices, potentially causing widespread disruptions.
Best Practices for Overcoming Challenges
To mitigate these risks, organizations should adopt best practices such as implementing strong authentication protocols, regularly updating firmware, and monitoring device activity for suspicious behavior.
Implementing Secure Remote IoT Device Login
Implementing secure remote IoT device login requires a comprehensive approach that addresses all aspects of device security. Below are the key steps to achieving this goal.
Step 1: Device Authentication
Device authentication ensures that only authorized devices can access the network. This can be achieved through methods such as certificates, tokens, or biometric authentication.
Read also:Penelope Menchaca A Rising Star In The World Of Entertainment
Step 2: Data Encryption
All data transmitted between devices and the cloud should be encrypted to prevent unauthorized access. This can be achieved using protocols such as TLS or SSL.
Step 3: Regular Updates
Regularly updating device firmware and software is essential to patch vulnerabilities and enhance security.
Role of IoT Core in Secure Device Login
IoT Core plays a crucial role in facilitating secure remote IoT device login. Its robust features and capabilities make it an ideal platform for managing IoT security.
Device Authentication with IoT Core
IoT Core provides robust device authentication mechanisms, ensuring that only trusted devices can connect to the network. This is achieved through the use of certificates and other authentication methods.
Monitoring and Management
IoT Core offers tools for monitoring device activity and managing device security. These features enable administrators to detect and respond to potential threats in real-time.
Best Practices for Secure IoT Deployment
Implementing secure IoT deployments requires adherence to best practices that address all aspects of device security. Below are some key recommendations.
Network Segmentation
Segmenting IoT devices into separate networks can help isolate potential threats and limit their impact.
Regular Audits
Conducting regular security audits ensures that all devices and systems comply with security standards and identifies potential vulnerabilities.
Tools and Technologies for Secure IoT
Several tools and technologies can enhance the security of IoT devices. Leveraging these solutions can significantly improve the overall security posture of IoT ecosystems.
IoT Security Frameworks
Frameworks such as the IoT Security Foundation provide guidelines and best practices for securing IoT devices. These frameworks can serve as valuable resources for organizations looking to enhance their IoT security.
Encryption Protocols
Using strong encryption protocols such as AES or RSA ensures that all data transmitted between devices and the cloud remains secure.
Case Studies and Real-World Examples
Examining real-world examples of secure IoT deployments can provide valuable insights into effective security practices. Below are some notable case studies.
Case Study 1: Smart City IoT Deployment
A smart city project in Europe successfully implemented secure IoT protocols, ensuring the safety and privacy of citizens' data. By leveraging IoT Core and other security technologies, the city was able to create a secure and efficient IoT ecosystem.
Case Study 2: Industrial IoT Security
An industrial company enhanced its IoT security by implementing robust authentication and encryption protocols. This resulted in improved operational efficiency and reduced the risk of cyberattacks.
Data and Statistics
Data and statistics play a critical role in understanding the importance of secure IoT deployments. Below are some key findings from recent studies.
- According to a report by Gartner, the number of IoT devices is expected to exceed 25 billion by 2030.
- A study by IBM found that 75% of organizations experienced an IoT-related security breach in the past year.
Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and trends. Staying informed about these developments is essential for maintaining secure IoT ecosystems.
Artificial Intelligence in IoT Security
AI-powered security solutions are becoming increasingly popular in IoT deployments. These solutions can detect and respond to threats in real-time, enhancing overall security.
Blockchain for Secure IoT
Blockchain technology offers promising solutions for securing IoT devices. Its decentralized nature ensures that data remains secure and tamper-proof.
Conclusion
In conclusion, secure remote IoT device login using IoT Core is a critical aspect of maintaining secure IoT ecosystems. By understanding the challenges and implementing best practices, organizations can protect their devices and data from potential threats. We encourage you to share your thoughts and experiences in the comments section below and explore other articles on our site for more insights into IoT security.
Table of Contents
- Understanding IoT Core and Its Importance
- Challenges in Secure Remote IoT Device Login
- Implementing Secure Remote IoT Device Login
- Role of IoT Core in Secure Device Login
- Best Practices for Secure IoT Deployment
- Tools and Technologies for Secure IoT
- Case Studies and Real-World Examples
- Data and Statistics
- Future Trends in IoT Security
- Conclusion