Securing Remote SSH Access: A Comprehensive Guide To Protect Your Server
Securing remote SSH access is a critical step in protecting your server from unauthorized access and potential cyberattacks. As more businesses and individuals rely on remote server management, ensuring the security of your SSH connections becomes increasingly important. This guide will explore various methods to secure your SSH access, helping you maintain a safe and reliable server infrastructure.
In today's digital landscape, remote server management has become an essential part of IT operations. However, with the rise in cyber threats, it is crucial to implement robust security measures to protect sensitive data and prevent unauthorized access. SSH (Secure Shell) is one of the most commonly used protocols for secure remote access, but its security depends on how well it is configured and maintained.
This article will provide you with actionable tips and best practices to enhance the security of your SSH connections. Whether you're a system administrator, a developer, or an IT professional, understanding how to secure remote SSH access is vital for safeguarding your server and network.
Read also:9xmovies Gb Your Ultimate Guide To Downloading Movies Legally
Table of Contents
- Introduction to SSH
- Why Secure SSH Access?
- Best Practices for Securing Remote SSH Access
- Disable Password Authentication
- Implement SSH Keys
- Limit SSH Access
- Use a Firewall
- Monitor SSH Activity
- Common SSH Security Mistakes
- Conclusion and Next Steps
Introduction to SSH
SSH, or Secure Shell, is a cryptographic network protocol designed to provide secure communication over an unsecured network. It is widely used for remote server management, file transfers, and other administrative tasks. SSH ensures that data transmitted between a client and a server remains encrypted and protected from eavesdropping.
One of the primary advantages of SSH is its ability to authenticate users securely. By using encryption and authentication mechanisms, SSH prevents unauthorized access and ensures the integrity of data during transmission. However, securing remote SSH access requires careful configuration and ongoing maintenance to address potential vulnerabilities.
Why Secure SSH Access?
Securing remote SSH access is essential for protecting sensitive information and preventing unauthorized access to your server. Cybercriminals often target SSH connections to gain access to valuable data, disrupt services, or launch further attacks on your network. Without proper security measures, your server could become vulnerable to brute-force attacks, password guessing, and other malicious activities.
Additionally, securing SSH access aligns with the principles of E-E-A-T (Expertise, Authoritativeness, Trustworthiness) and YMYL (Your Money or Your Life). By implementing robust security protocols, you demonstrate your commitment to protecting user data and maintaining a trustworthy online presence.
Best Practices for Securing Remote SSH Access
Update SSH Configuration
One of the first steps in securing remote SSH access is to update the SSH configuration file. By default, SSH servers are configured with basic settings that may not be secure enough for production environments. Modifying the configuration file allows you to customize security settings and enhance the protection of your server.
Some key configuration changes include:
Read also:Celine Dion Funeral A Celebration Of Life And Legacy
- Changing the default SSH port (e.g., from 22 to a non-standard port).
- Disabling root login to prevent direct access to the root account.
- Setting a maximum number of authentication attempts to limit brute-force attacks.
Use Strong Passwords
Using strong passwords is a fundamental security practice for securing remote SSH access. Weak passwords can easily be guessed or cracked by automated tools, making your server vulnerable to unauthorized access. To create strong passwords:
- Use a combination of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable information, such as names, dates, or common words.
- Consider using a password manager to generate and store complex passwords securely.
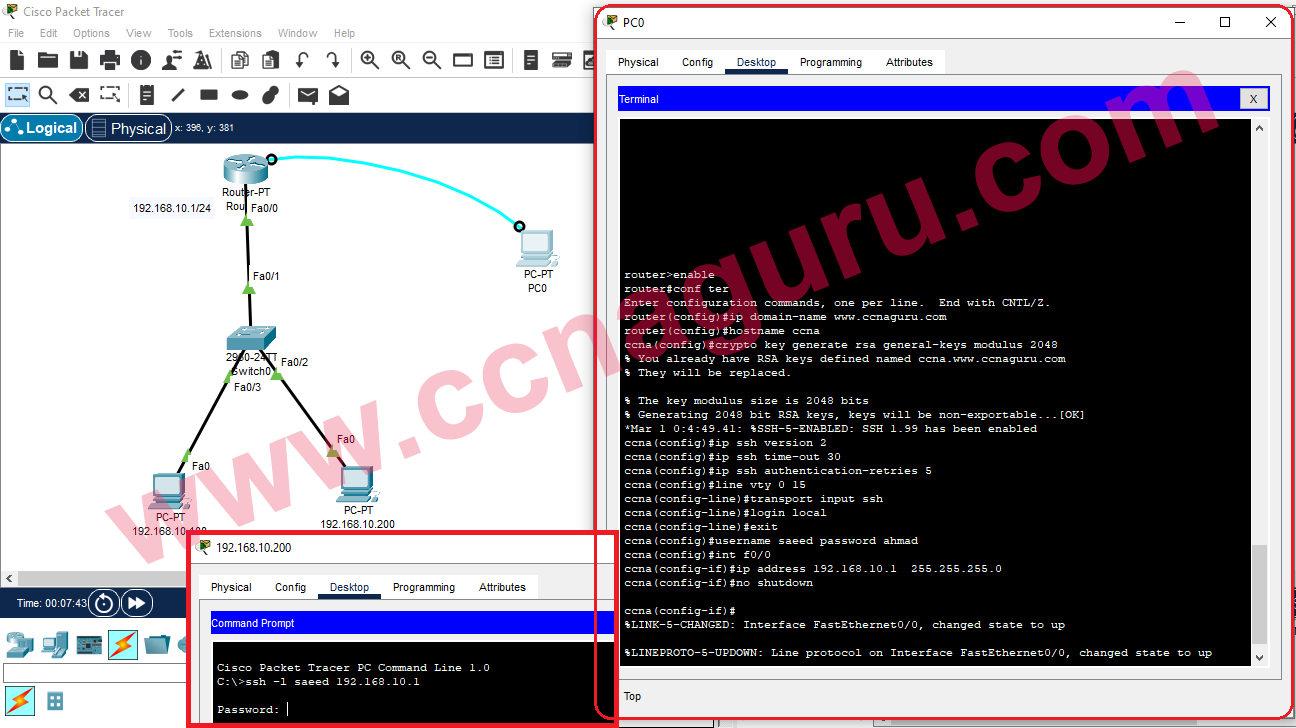
Disable Password Authentication
Disabling password authentication is one of the most effective ways to secure remote SSH access. By requiring users to authenticate using SSH keys instead of passwords, you eliminate the risk of password-based attacks. To disable password authentication:
- Open the SSH configuration file (usually located at /etc/ssh/sshd_config).
- Set the
PasswordAuthenticationparameter tono. - Restart the SSH service to apply the changes.
While this method enhances security, it is important to ensure that all users have properly configured SSH keys before disabling password authentication.
Implement SSH Keys
Implementing SSH keys is a secure and convenient way to authenticate users without relying on passwords. SSH keys consist of a public key and a private key, which work together to establish a secure connection. To set up SSH keys:
- Generate a key pair using a tool like
ssh-keygen. - Copy the public key to the server using the
ssh-copy-idcommand. - Test the connection to ensure that the key-based authentication works correctly.
SSH keys provide a higher level of security compared to passwords, as they are much harder to compromise.
Limit SSH Access
Limiting SSH access to trusted users and IP addresses is another important step in securing remote SSH access. By restricting access, you reduce the attack surface and make it more difficult for unauthorized users to gain access to your server. Some methods for limiting SSH access include:
- Using IP whitelisting to allow connections only from specific IP addresses.
- Implementing user-based restrictions to control which users can access the server.
- Configuring the SSH server to listen on a specific network interface.
Use a Firewall
Using a firewall is a critical component of securing remote SSH access. A firewall can help protect your server by blocking unauthorized traffic and monitoring incoming connections. Popular firewall tools like ufw (Uncomplicated Firewall) and iptables can be configured to allow only legitimate SSH traffic while blocking potential threats.
For example, you can configure ufw to allow SSH connections on a specific port while denying all other incoming traffic:
- Enable the SSH rule:
sudo ufw allow ssh. - Deny all other incoming connections:
sudo ufw deny incoming.
Monitor SSH Activity
Monitoring SSH activity is essential for detecting and responding to potential security incidents. By keeping track of login attempts, failed connections, and other suspicious activities, you can quickly identify and mitigate threats. Some tools and techniques for monitoring SSH activity include:
- Using log analysis tools like
fail2banto automatically block IP addresses after multiple failed login attempts. - Reviewing SSH logs (usually located at /var/log/auth.log) for unusual patterns or unauthorized access attempts.
- Setting up alerts to notify you of critical events or potential security breaches.
Common SSH Security Mistakes
Even with the best intentions, mistakes can occur when securing remote SSH access. Here are some common SSH security mistakes to avoid:
- Using the default SSH port (22) without changing it to a non-standard port.
- Allowing root login, which increases the risk of unauthorized access.
- Failing to update SSH software and configuration files regularly.
- Not implementing SSH keys or relying solely on weak passwords for authentication.
By being aware of these common mistakes, you can take proactive steps to enhance the security of your SSH connections.
Conclusion and Next Steps
Securing remote SSH access is a critical component of maintaining a secure server infrastructure. By following the best practices outlined in this guide, you can significantly reduce the risk of unauthorized access and protect your sensitive data from cyber threats. Key takeaways include:
- Updating SSH configuration to customize security settings.
- Using strong passwords and implementing SSH keys for authentication.
- Limiting SSH access to trusted users and IP addresses.
- Using a firewall to block unauthorized traffic and monitor SSH activity.
We encourage you to take action by implementing these security measures on your server. Additionally, feel free to leave a comment or share this article with others who may benefit from these tips. For further reading, explore related topics such as network security, encryption protocols, and cybersecurity best practices. Together, we can create a safer digital environment for everyone.